Viruses and malware: are we protecting ourselves adequately?
On August 10 2017Télécom SudParis


Cybersecurity incidents are increasingly gaining public attention. They are frequently mentioned in the media and discussed by specialists, such as Guillame Poupard, Director General of the French Information Security Agency. This attests to the fact that these digital incidents have an increasingly significant impact on our daily lives. Questions therefore arise about how we are protecting our digital activities, and if this protection is adequate. The publicity surrounding security incidents may, at first glance, lead us to believe that we are not doing enough.
A look at the current situation
Let us first take a look at the progression of software vulnerabilities since 2001, as illustrated by the National Vulnerability Database (NVD), the reference site of the American National Institute of Standards and Technology (NIST).
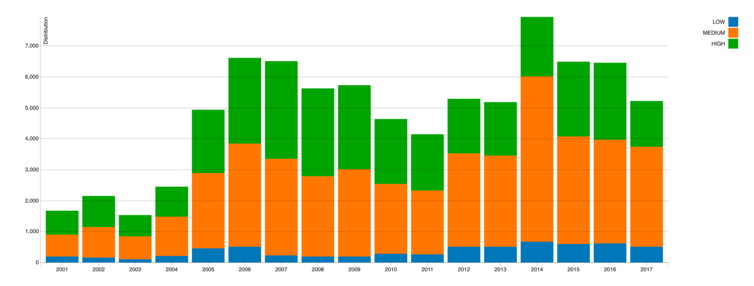
Upon an analysis of the distribution of vulnerabilities to computer-related attacks, as published by the American National Institute of Standards and Technology (NIST) in visualizations on the National Vulnerability Database, we observe that since 2005, there has not been a significant increase in the number of vulnerabilities published each year. The distribution of risk levels (high, medium, low) has also remained relatively steady. Nevertheless, it is possible that the situation may be different in 2017, since, just halfway through the year, we have already reached publication levels similar to those of 2012.
It should be noted, however, that the growing number of vulnerabilities published in comparison to before 2005 is also partially due to a greater exposure of systems and software to attempts to compromise and external audits. For example, Google has implemented Google Project Zero, which specifically searches for vulnerabilities in programs and makes them public. It is therefore natural that more discoveries are made.
There is also an increasing number of objects, the much-discussed Internet of Things, which use embedded software, and therefore present vulnerabilities. The recent example of the “Mirai” network demonstrates the vulnerability of these environments which account for a growing portion of our digital activities. Therefore, the rise in the number of vulnerabilities published simply represents the increase in our digital activities.





